Newspaper canard leads to federal trojan horse

Today, the AK Vorrat published their statement on Minister of Justice Brandstetter’s proposal to introduce a governmental monitoring software (Federal Trojan). The detailed legal and technical statement shows, why this ad hoc legislation causes more problems than it can solve.
The use of governmental monitoring software, as is the Ministry of Justice’s plan, is an unduly interference with fundamental rights, which is neither appropriate nor necessary and certainly not proportionate. The draft of this law has been ready since November 2015 and is to be whipped through Parliament now, after the attacks of Brussels, as ad hoc legislation, just like they tried before with the “Police State-Protection Act”.
“It seems that the Justice Department was in such a hurry to use the atrocious terrorist attack for a tightening of surveillance laws, that there wasn’t even time to remove the reference to a proven hoax in November from the notes to the law,” said Thomas Lohninger from AKVorrat.
Contrary to statements by Justice Minister Brandstetter, the legal text submitted by him also allows for remote installation on the target system without physical access.
The monitoring of a target system is only possible by taking advantage of unclosed security holes. Through the purchase of such monitoring software, the illegal market for vulnerabilities is thus co-financed with tax money. Contrary to the clear responsibility to quickly close security holes in the interest of the population, with this, the state has an interest to leave these security flaws unprotected. In view of the enormous importance of IT security in modern society, economy and democracy, this action is plainly irresponsible.

“For 450,000 euros per year, spy software is to be purchased, which promotes the illegal market for unclosed security holes, while at the same being very likely to be discovered, if the target computer – for any reason whatsoever – has high data security,” says Christof Tschohl, chairman of AKVorrat. “Professional criminals can then purposefully lead the investigators onto the wrong track or, in the worst case, even hack into the authorities’ systems via possible vulnerabilities within the Federal Trojan”, the communications engineer and lawyer concretized his concerns.
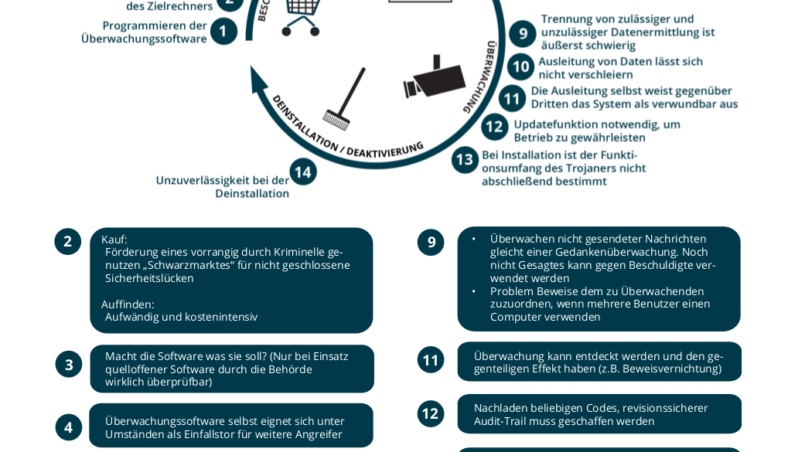
In the expositions for the Law it is explicitly pointed out that only “online monitoring” of messages sent and contacts stored should be enabled, while an “online search” of the entire computer remains illegal. However, such a distinction is technically hardly possible. To monitor communications on a computer prior to encryption or to extract contacts, it must first be analyzed what software is in use and what files are present on the computer. In addition, continuous monitoring of system functions which are independent of the communication has to take place, in order to intercept data before encryption. This monitoring of mental content will thus take place at a time when it is unclear whether this content is ever transmitted to third parties. So statements merely formulated but never released can already be used against a person. The Federal Trojan is therefore paving the way to a “thought police” and is incompatible with the idea of the rule of law.
Translation from German: Serena Nebo
Credits
| Image | Title | Author | License |
|---|---|---|---|
 |
Newspaper hoax leads to the Bundestrojaner | AK Vorrat | CC BY 4.0 |
